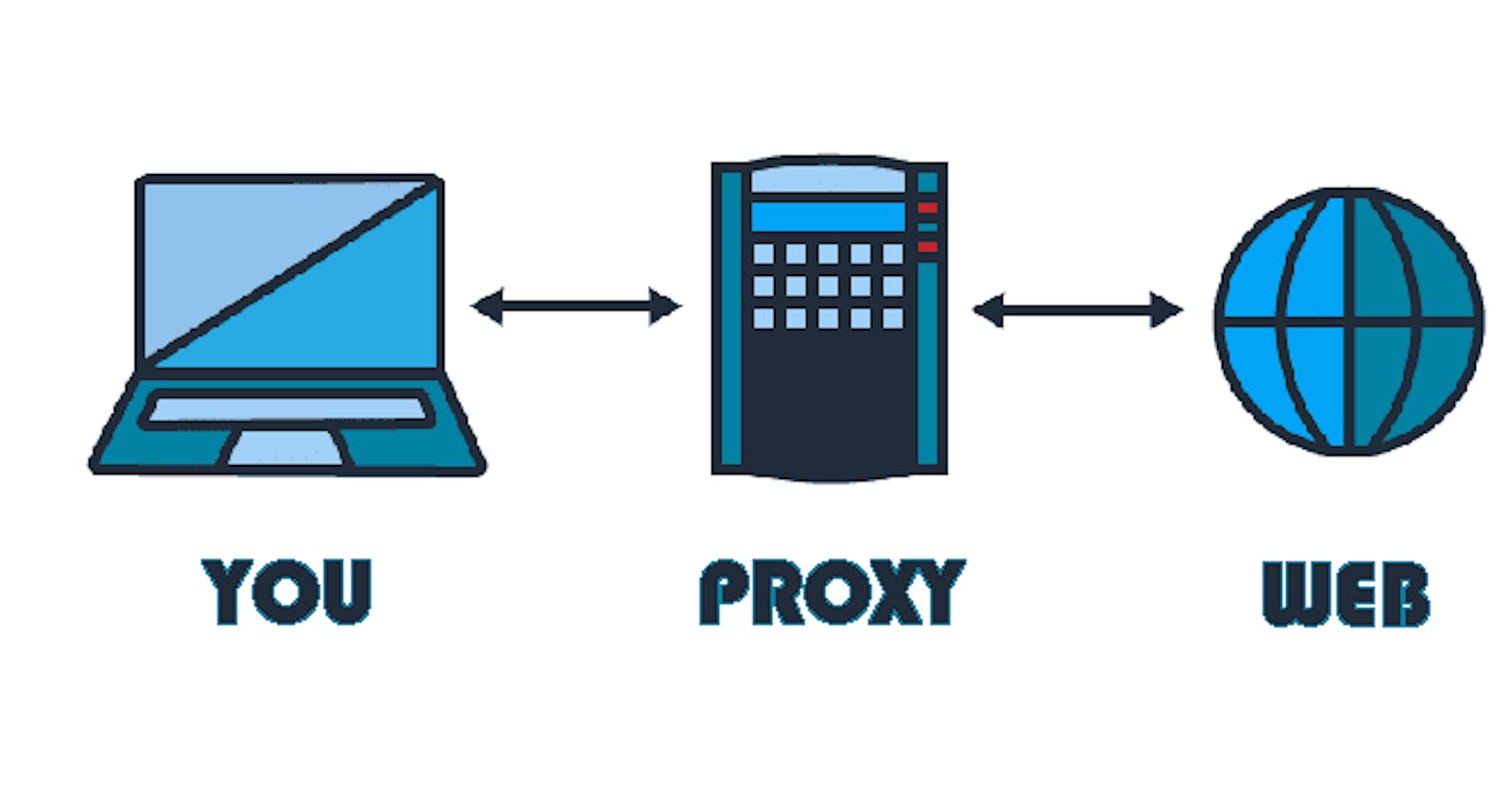
What is a Proxy server ?
A Proxy server is a server application that acts as an intermediary between a client requesting a resource and a server providing that resource.
Requests sent by clients are sent to the proxy server rather than the response server.
It evaluates the request and performs the required network transactions
Types
1) Forward Proxy
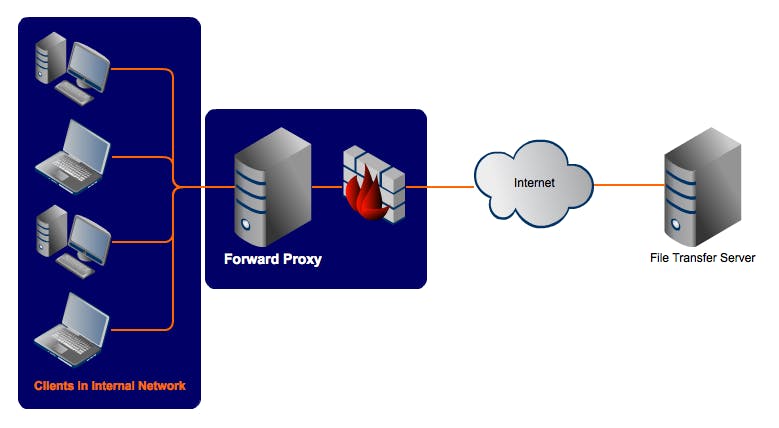
Whenever user request something to the internet, it does not directly go to the internet.
The forward proxy acts on behalf of user, forwarding request from user to internet.
Use case:-
- Used in corporate or schools to control internet access for users.
Examples:-
Squid
Apache HTTP Server
Forefront Threat Management Gateway
Privoxy
TinyProxy
CCProxy
WinGate Proxy Server
Dante
Polipo
Shadowsocks
2) Reverse Proxy
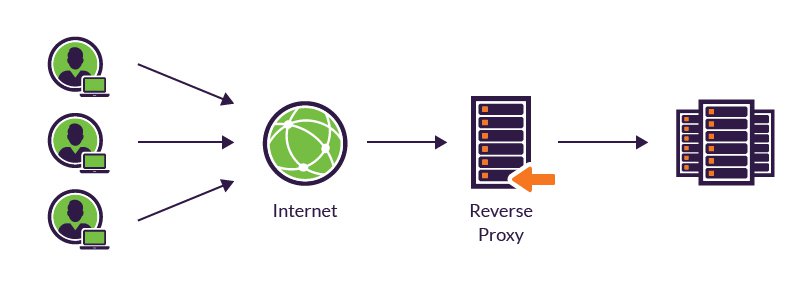
It sits in front of server and receives request on their behalf.
It then forwards this requests to server and returns the server response to user.
Use case :-
Enhance security by shielding servers from direct internet exposure.
Enable load balancing across multiple servers.
Example:-
Nginx
HAProxy
Apache HTTP Server (with mod_proxy module)
Envoy Proxy
Traefik
Caddy
Pound
Varnish Cache
AWS Application Load Balancer (ALB)
Microsoft Application Request Routing (ARR)
Future Trends in Proxy technology
Containerized Proxy
Enable organizations to deploy proxy instances quickly, scale them dynamically based on demand, and streamline management through container orchestration platforms.
Cloud-based Proxy services
Eliminate the need for organizations to maintain and manage their proxy infrastructure, providing benefits such as elasticity, cost-effectiveness, and global scalability.
Integration with AI and ML
By analyzing network traffic in real-time, AI-powered proxies can identify and block suspicious activities.